Question
How many persons completed the training between G and
C? Study the following information carefully and answer the questions given below. Eight persons A, B, C, D, E, F, G and H completed Army training in eight different years viz. 2012 to 2019, but not necessarily in the same order. D completed the training three years after F. Only three persons completed the training between C and F. C doesn’t complete on an odd numbered year. The number of persons completed before D is one more than the number of persons completed after B. Only one person completed the training between B and A. The difference between the years in which G and E completed is three years. Both H and E completed the training in consecutive years.Solution
We have, D completed the training three years after F. Only three persons completed the training between C and F. C doesn’t complete on an odd numbered year. From the above condition, there are three possibilities 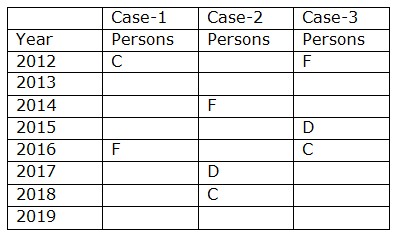 Again we have, The number of persons completed before D is one more than the number of persons completed after B. Only one person completed the training between B and A.
Again we have, The number of persons completed before D is one more than the number of persons completed after B. Only one person completed the training between B and A. 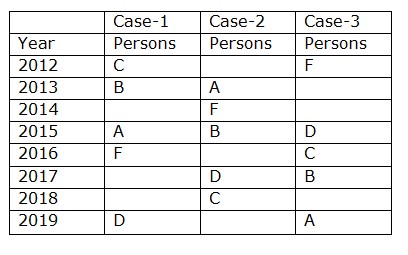 Again we have, The difference between the years in which G and E completed is three years. Both H and E completed the training in consecutive years. So Case2 and 3 get eliminated, hence the final arrangement becomes
Again we have, The difference between the years in which G and E completed is three years. Both H and E completed the training in consecutive years. So Case2 and 3 get eliminated, hence the final arrangement becomes 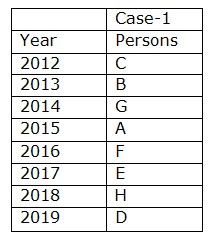
निम्नलिखित संज्ञाओं में से पुल्लिंग की पहचान कीजिए:
(A) घ...
निम्नलिखित कहानियों में से प्रेमचंद की कहानी कौन-सी नहीं �...
‘ दीप्ति’ का पर्यायवाची है—
वसुदेव के पुत्र
'इतिहास का जानकार' के लिए निम्नलिखित में से कौनसा शब्द �...
निम्नलिखित शब्दों में से एक का अर्थ ' घन ', ' मतलब ', ' कारण ' और ' �...
निम्नलिखित प्रश्न में विषम शब्द का चयन करे ?
' पुराना ' किस प्रकार का विशेषण है ?
निम्नलिखित मे से अशुद्ध वाक्य को चिन्हित कीजिए –
Manuscript’ शब्द का अर्थ है –
Relevant for Exams:


