Question
Read the directions carefully and answer the following
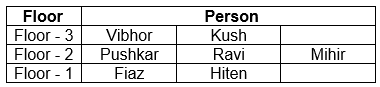
questions. Seven person Pushkar, Fiaz, Ravi, Vibhor, Mihir, Kush, and Hiten live in a three floored building. Two people live with Pushkar, who lives on an even numbered floor. Ravi and Mihir live on the same floor with one other on the same floor. Fiaz lives below Ravi. Vibhor does not live on the bottommost floor. Kush lives above Hiten. Who among the following above Ravi?Solution
Raghav Chadha is a Rajya Sabha member from which of the following Political Parties?
Who is the first woman president of table tennis federation of India appointed recently?
Jajam / Aazam print is famous of -
How many Lok Sabha Constituencies does Gujarat have in the seventeenth Lok Sabha?
In which year was the Consumer Protection Bill passed by the houses of Parliament?
MALDA gap separates?
- What is the currency of Japan?
Which of the following is a thermal power station of Uttar Pradesh?
The statements of estimated receipts and expenditure of the Government of India is presented to the Parliament every year as per ____of the Indian Const...
Bhadla Solar Park is located at -
Relevant for Exams:


