Start learning 50% faster. Sign in now
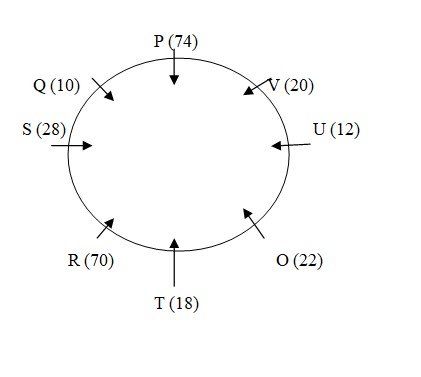
The age of the second eldest person is 70 year which means the age of the grandmother is 70 year. V is the brother – in- law of O. V’s age is 2 year less than O’s age and O’s age is 6 year less than S’s age. R is the mother of S and her age is 2.5 of the age of her son. From these it is clear that O, V and S belongs to second generation and R is the grandmother whose age is 70 year. Further, only the father of T is sitting between Q and V. T does not belong to third generation. So, T belongs to second generation. The person who is sitting on the immediate left of O and immediate right of R is 18 year old while Q is 10 year old. S, who is sitting next to Q, is not sitting opposite to O. 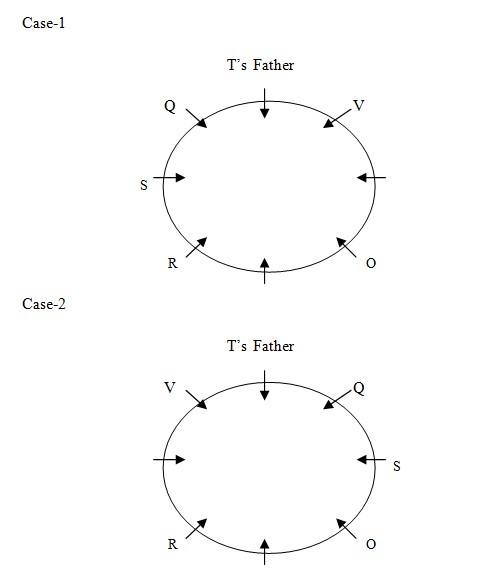 Q is the female member of the family. Q is 10 year old. So, Q is the granddaughter and 10 year old. R is 4 year younger than P. Means P is 74 year old. Rest U’s age is multiple of 4 but not a perfect square. As only remaining position is that U is the grandson and is 12 year old. The person who sits immediate right of V is a male but he is not U. So, from this case 3 will be eliminated. As we know that U can’t sit between R and O, so clearly T sit between R and O and U can’t sit to immediate right of Q so from this case 2 will be eliminated. Rest we know that the age of T is 18 year so she is the daughter of P and S is the son of R and is 28 year old. Rest V is 20 year old, O is 22 year old, O is 22 year old. So, the final arrangement is –
Q is the female member of the family. Q is 10 year old. So, Q is the granddaughter and 10 year old. R is 4 year younger than P. Means P is 74 year old. Rest U’s age is multiple of 4 but not a perfect square. As only remaining position is that U is the grandson and is 12 year old. The person who sits immediate right of V is a male but he is not U. So, from this case 3 will be eliminated. As we know that U can’t sit between R and O, so clearly T sit between R and O and U can’t sit to immediate right of Q so from this case 2 will be eliminated. Rest we know that the age of T is 18 year so she is the daughter of P and S is the son of R and is 28 year old. Rest V is 20 year old, O is 22 year old, O is 22 year old. So, the final arrangement is – 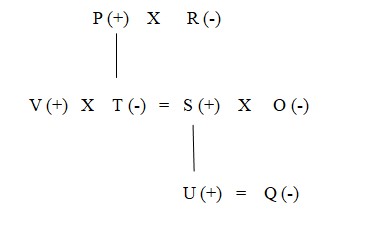
Which plant has stomata only on the upper surface of its leaves?
How many ATP molecules are required in the C₄ pathway for the synthesis of one molecule of glucose?
Which experiment demonstrated that food is translocated through the phloem?
Which type of sugar is most commonly transported during phloem translocation?
Agricultural census is conducted by Ministry of Agriculture and Farmers’ Welfare in every ___ year with participation of states and UTs since 1970 as ...
The first stable compound formed in the photosynthesis of C3 plants is:
The Structural and functional unit of chromosome is termed as
In the following given options, What is the importance of mitosis cell division?
Which statement about transpiration is true?
Which among the following is Photoblastic Seed?