Question
How many seats are there around the
table? Study the following information carefully and answer the questions given below: A certain number of persons are sitting around the circular table. All of them are facing towards the center. Three persons sit between A and K who sits second to the left of C. E sits to the immediate left of G who sits second to the left of M. M sits third to the left of I who sits an immediate neighbour of K. Both E and A sit adjacent to each other. The number of persons sits between G and K is one less than the number of persons sits between K and E when counted from the right of both G and K respectively. At least one person sits between C and E when counted from the right of C.Solution
STEP I: M sits third to the left of I who sits an immediate neighbour of K. Three persons sit between A and K who sits second to the left of C. As per these statements, we can say that there are three possible cases and the arrangement will look like this: 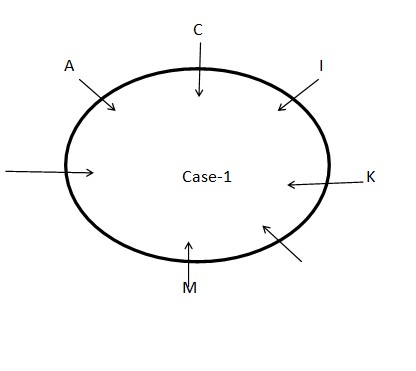
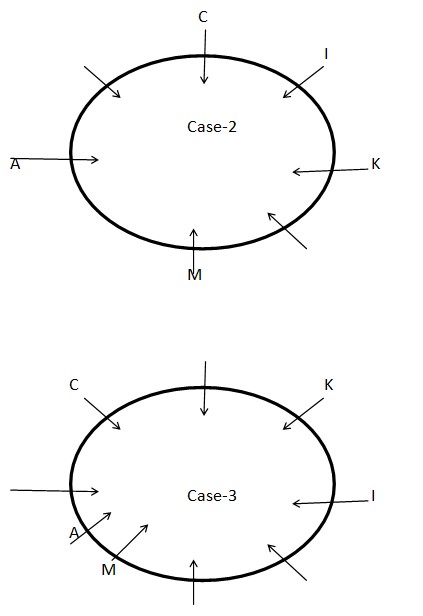 STEP II: E sits to the immediate left of G who sits second to the left of M. Both E and A sit adjacent to each other. The number of persons sits between G and K is one less than the number of persons sits between K and E when counted from the right of both G and K respectively. At least one person sits between C and E when counted from the right of C. As per these statements, CASE I and CASE III get eliminated and we continue with CASE II and the final arrangement will look like this:
STEP II: E sits to the immediate left of G who sits second to the left of M. Both E and A sit adjacent to each other. The number of persons sits between G and K is one less than the number of persons sits between K and E when counted from the right of both G and K respectively. At least one person sits between C and E when counted from the right of C. As per these statements, CASE I and CASE III get eliminated and we continue with CASE II and the final arrangement will look like this: 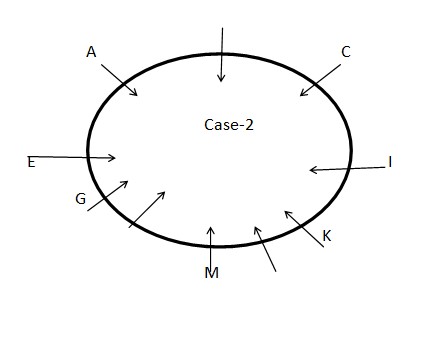
What is India’s rank globally in Aluminium production?
How many types of the amendment are mentioned by the Indian Constitution as per Article 368?
What was the fate of Bahadur Shah Zafar, the last Mughal Emperor, after the revolt was suppressed?
How many days are organized for the modern Olympic Games?
In honour of an Indian musician, the US state of Massachusetts proclaimed 20 April as __________ in 1984.
Under which article was the Right of Children to Free and Compulsory Education (RTE) Act, 2009, introduced to provide every child with the right to full...
Sanchar Saathi portal is an initiative, which aims to enhance the ________________?
Sarus Crane, recently seen in the news, is the official bird of which state?
Approximately how much percentage (nearest to integer) of total water on the surface of earth is accounted for by the oceans?
Who is the winner declared when the weightlifting competition is tie?
Relevant for Exams:



