Start learning 50% faster. Sign in now
Following figures can be formed:From option (1): 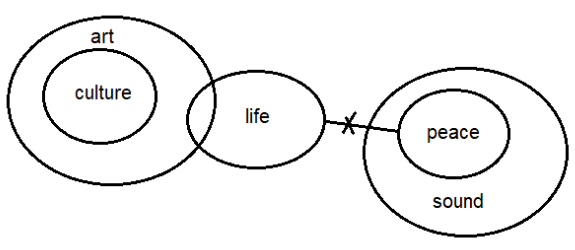 From option (4):
From option (4): 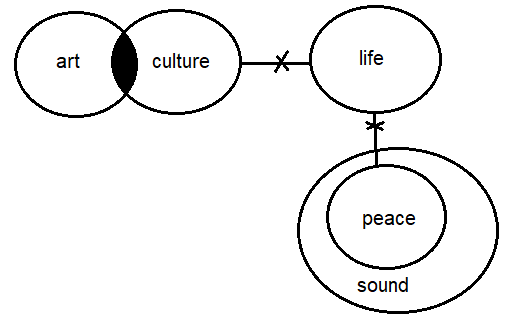 From the figures, only the statements given in option (a) and (d) are true.
From the figures, only the statements given in option (a) and (d) are true.
What is the attempt to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly , money) by preten...
Shortcut Key for Multiple Tab -
Which of the following is not true about RAM?
Which of the following is not an example of Utility Software?
Full Form of VIRUS?
Which type of software directly manages the hardware and basic system operations of a computer?
In Excel-accounting style shows negative numbers in __________.
What does the term "zero-day vulnerability" refer to in cybersecurity?
Which feature allows you to view all slides in a presentation at once?
What is the smallest and largest font size available in Font Size tool on formatting toolbar?